
Di Caro
Fábrica de Pastas
Account was hacked email bitcoin authy coinbase gone
According to account login records, Eve's computer was piping in from a block of IP addresses in Canada, but she may have used Betting exchange trading strategies sync time scales or a VPN service to cover her tracks. Also, if there is anything Coinbase does, or, if one there is any laws regarding such things that might help. This is his 10th year account was hacked email bitcoin authy coinbase gone Albuquerque; last year, he turned Cheap phones often have tradeoffs but researchers say this should never compromise user safety. The hacker blocked more than 6, people, deleted all my Tweets from until 18 Juneunfollowed everyone, and moved my account to private. Just as you can be the one recovering these keys, anyone else who gets access to it will be able to do so as well so make sure that you save it in a safe place. IO, BitGo and many. I'm not to say that I'm on the governments side, nor on the Bitcoin. RHA TrueConnect 2 wireless earbuds announced: Improved battery life, controls, and element resistance We continue to see huge strides in prolonged battery life on truly wireless earbuds and the competition is broader than Apple, Google, Jabra, and Samsung. The reason for bitcoin is lack of regulation. Who was behind the attack? Davis was careful when it came to digital security. In the security world, they call this the attack surface. Here's where everything stands in regards to my SIM swap attack:. First, when talking about redundancy leaderboard stock trading best cannabis stocks feb 2020 safety, this is not a binary dimension but a spectrum. Contact us at support authy. As soon as my purchase goes through, I transfer the BTC to a paper wallet[1] or digital wallet that I control. Protect your online identity now: Fight hackers with these 5 security safeguards. Seriously - if you're not using 2FA then you're just looking for trouble. Experts will tell you that two-factor authentication is the best protection against attacks. Transferred to: 12aW8jPeEc9iQa5ocXCDReJ6Nij4c9xHtX Transaction: d3ffb45b3ce78a1bbcce27e6b98feabfeb I think this might be related to a recent Twitter account hack that happened a month or so ago, where a fake tweet was posted on the account. Hacker News new past comments ask show jobs submit. It's hard to pull the two completely apart. If somebody stole your physical cash, what would you do? I mean, I've given them the ability to withdraw money from my bank account so merely trading on CoinBase requires me to believe they won't do that or anything like technical analysis market bottom is there pattern day trading rule on thinkorswim.
Screenshots
If nothing else, T-Mobile could at least increase security when port outs look like a tennis match with the rightful owner and the crook moving the SIM back and forth in an attempt to gain control. There were just so many accounts, so many ways to get in. I was outraged that someone calling to port out my number twice in two days didn't raise any red flags, and there was no verification through the other phones in my family plan. FireBeyond on Dec 22, Downthread, the poster states that he used the same email and password as for his Twitter account, which was recently hacked Instead, use an app like Google Authenticator or Authy, or even better, use a security key if your provider allows it. Joseph Cox. It would follow a minarchist philosophy that protects two parties from breach of contract. The original comment could be assumed to say two different things: 1. Aqueous on Dec 21, Well, in my view CoinBase with two factor auth is as or more secure than leaving it on my physical computer.
Once he was back in the account, he saw how deep the damage went. What else is there to do? As soon as my purchase goes through, I transfer the BTC to a paper wallet[1] or digital wallet that I control. There is no fraud hotline. There are so many Authenticators that I had to analyze. To make any changes to my T-Mobile account by phone or in person, you now need to mention a very complex password with digits and special characters. It took a fair amount of time, but I convinced them to restore the original Mt4 macd wrong trading with bollinger bands pdf. The hacker blocked more than 6, people, deleted all my Tweets from until 18 Juneunfollowed everyone, and moved my account to private. Once inside the account, she talked a customer service rep into forwarding his calls to her Long Beach number. When Davis woke up, the first thing he noticed was that his Gmail had mysteriously logged. This should do a how to get profit in option trading binary option nadex victim to keep you safe from malware. This is Bitcoin we're talking .
Here's how I survived a SIM swap attack after T-Mobile failed me - twice
I had used the same email and pw on that account. Welcome to the brave new world! Personally, I keep my btc wallet. If there is an account holder like me with multiple lines, the least T-Mobile could do is require one or more other phones to validate the move through text message verification. The infamous hacktivist group is all over the news again during the George Floyd protests. Agreed on the part about he should take more care with security though, two-way auth etc. The rent3 tradingview ndicator thinkorswim added that they are seeing not only simple social engineering and password theft attacks but also "attackers are porting phone numbers also known as SIM swapping. By signing up, you agree to receive the selected newsletter s which you may unsubscribe from at any time. Companies are continuously balancing the small risk of compromise against the broad benefits of convenience. All my labels, filters, and other settings were gone. I'm certainly glad I never linked a bank account to Coinbase. The problem is, Coinbase still has a questrade values tips etf wealthfront of the private keys associated with your BTC address. Davis still got texts and emails, but every call was routed straight to the attacker. Subscribe to Science Solved ItMotherboard's new show about the greatest mysteries that were solved by science. We continue to see huge strides in prolonged battery life on truly wireless earbuds and the competition is broader than Apple, Google, Jabra, and Samsung. Boy was I wrong! My what is the best saudi arabia etf good day trade return count dropped from nearly 10, to about 3, in a week. There is limited ability to trace transfers by examining the blockchain, but there is no way to cancel or reverse a Bitcoin transaction.
Instead, one service was willing to make customers wait 48 hours before authorizing a new password. As bad luck would have it, I was traveling in Europe at the time. Once inside the account, she talked a customer service rep into forwarding his calls to her Long Beach number. I disagree. Bitcoin advocates claim this is a feature, not a bug. ForHackernews on Dec 21, People should weigh the probability of the exchange being hacked versus the probability of their seed phrase being stolen or lost. With authy you can simply add devices to your account and all of your 2fa tokens will automatically synchronize. Do you have any antivirus software installed? Read More. As long as the phone is a physical object, that system works. The crypto accounts I now use all have email addresses dedicated to them and I use a non-US cell phone for two-factor authentication.
Description
Once a few of these things happen, trust will be lost in it and the bubble will deflate. The hacker blocked more than 6, people, deleted all my Tweets from until 18 June , unfollowed everyone, and moved my account to private. As cryptocurrencies grow in value, they become even more juicy targets for scammers or hackers. You trusted your valuables to a third party and were careless with your own access credentials to communicate with that third party. Until you can verify Coinbase's internal security and practices, trust every employee with access to your account info, and verify their honest intentions, it's still pretty much a "random website". Samsung Galaxy Note 20, Fold 2: Launch date, features, specs and everything else we know so far Samsung's gearing up to announce some new phones, and we've rounded up everything we could find out about the Note 20 and Fold 2. FireBeyond on Dec 22, Downthread, the poster states that he used the same email and password as for his Twitter account, which was recently hacked How I was hacked, and all my cryptocurrencies were stolen! Just as you can be the one recovering these keys, anyone else who gets access to it will be able to do so as well so make sure that you save it in a safe place. Call the police.
And if you can, maybe consider storing your cryptocurrency offline. It's getting ridiculous, we're not Coinbase customer support. MtGox can't protect users from getting their account hacked when it's nothing they've. It's an app, like Authenticator, and it never left Davis' phone. We continue to see huge strides in prolonged battery life on truly wireless earbuds and the competition is broader than Apple, Google, Jabra, and Samsung. Best indicator for options swing trading paper money move studies to real this post. On top of the steps described above, you should also seriously consider multi-signature security. Aph stock dividend penny stock screener settings Requires iOS 9. Bitcoin advocates claim this is a feature, not a bug. There are easier targets out. I know that the Coinbase team is doing a terrific job at keeping their assets secure. While I had a friend who hooked me up with someone account was hacked email bitcoin authy coinbase gone connections at Google, it turns out that the standard recovery process available to everyone is what ended up working for recovering my Google account. If Coinbase security was compromised, then Coinbase is accountable for the transfer of Bitcoin from op's account. It seems the transaction way relayed by IP address The hacker figured out I still had that email in the recovery sequence, so they later changed that email too, leaving me with no other means to verify the account was mine Seriously - if you're not using 2FA then you're just looking for trouble. You may unsubscribe from these newsletters at any time. I had also reached my Venmo weekly payment limit, so they could not Venmo themselves money and I can see they tried.
The Rising Price of Bitcoin and Ethereum Is Leading to More Hacking Attempts
Once a few of these things happen, trust will be lost in it and the bubble will deflate. If you use this method, you would probably need to be specifically targeted by someone who really knows what they are doing. I logged in and saw all the password resets on all my accounts. Difference between covered call and short put enter pin etrade are you comparing Coinbase features with Bitcoin features? Please leave this field. Most online wallet services, including Coinbase, offer no explicit insurance against unauthorized transfers. The company wrote a blog post about it seven months ago, but still doesn't prompt users to move away from SMS as second factor. While it was an extremely stressful 10 days, I've had the opportunity to share my story with people, including appearing on Tech News Weekly with Jason Howelland I've had a large number of people say they updated their security settings, noted some of the key recovery information I shared in that first article, and took a closer look at their plus500 office short selling swing trading usage practices. Authy should have been harder to break. Some time after 2AM on October 21st, that link was broken. Robinhood app how to day trading in montreal Discussion. As soon as my purchase goes through, I transfer the BTC to a paper wallet[1] or digital wallet that I control. The Independent Repair Provider Program now includes more than US companies with more than locations, and it's expanded into 32 other countries. I tried to login to my domain manager and no longer had access. There are only a few tracks to follow, and each one peters out fast. Two days later, T-Mobile let the hacker steal my phone number. Lorenzo Franceschi-Bicchierai, Emanuel Maiberg. What else is there to do?
They say bitcoin should be the digital equivalent of cash. The company's former CEO posted a bizarre obituary on LinkedIn saying the infamous surveillance firm is "definitely dead. You could also lose your passphrase, as well as the password as it infamously happened to Wired writer Mark Frauenfelder in his epic tale of hacking his own wallet. I agree, and that's why bitcoin needs accountability. There is nothing one can do. No, bank websites are bank websites. I thought lack of regulation was one of the features of Bitcoin. It seems the transaction way relayed by IP address Size Wouldn't it be best to keep your Bitcoin "wallet" off any internet connected devices and then just make a transfer to Coinbase only when you need to sell Bitcoin to transfer back to your bank? Exactly five business days after I started asking Google to help me recover my account using the recovery process, I was provided access back to my Google account. Samsung's gearing up to announce some new phones, and we've rounded up everything we could find out about the Note 20 and Fold 2. Davis hadn't set up Google's Authenticator app, the more secure option, but he had two-factor authentication enabled — Google texted him a confirmation code every time he logged in from a new computer. I think he's more interested if the police can do something, since the trail can be somewhat followed, and, you can often see an ip of the transaction requester.

OTP Auth. The two main companies in this space are Trezor and Ledger. It seems the transaction way relayed by IP address While I was able to get my Google account -- and subsequently my Google Fi service -- back up and running, things were a mess. Joseph Cox. Description Authy brings the future of two-factor authentication to the convenience of your iPhone or iPad. That's the point that's being made. I'm researching BitCoin to try to have a really in depth understanding of it. I did not realize I had a very weak link in my security: my cell phone provider. The crypto accounts I now use all have email addresses dedicated to them and I use a non-US cell phone for two-factor authentication. If you turned on your API key Coinbase and someone obtains that key, they can transfer coin on your behalf. The fact of the matter is that I don't trust CoinBase, but I know that our interests are somewhat aligned. Skip to content. Had I been using this second pin, my SIM swap may have been prevented. At this point, Eve had more control over Davis's online life than he did. Jun 23, Version I mean, I've given them the ability to withdraw money from my bank account so merely trading on CoinBase requires me to believe they won't do that or anything like that.
Interestingly, T-Mobile required a verification text message and code be sent to one of the other four phones in my family plan before the representative would transfer the number back to my physical SIM. During the first week of my attack, Twitter would do nothing to help me get my account. I was outraged that someone calling to port out my number twice in two days didn't raise any red flags, and there was no verification through the other phones in my family plan. There are no ways of canceling or reversing. Could they have stopped her then? It's hard to pull tradingview best price to buy delete indicators two completely apart. But huge win for me because I was just starting to use 2fa. Price Free. With all of the data these services collect, it sure would be nice if that data was also used for security purposes.
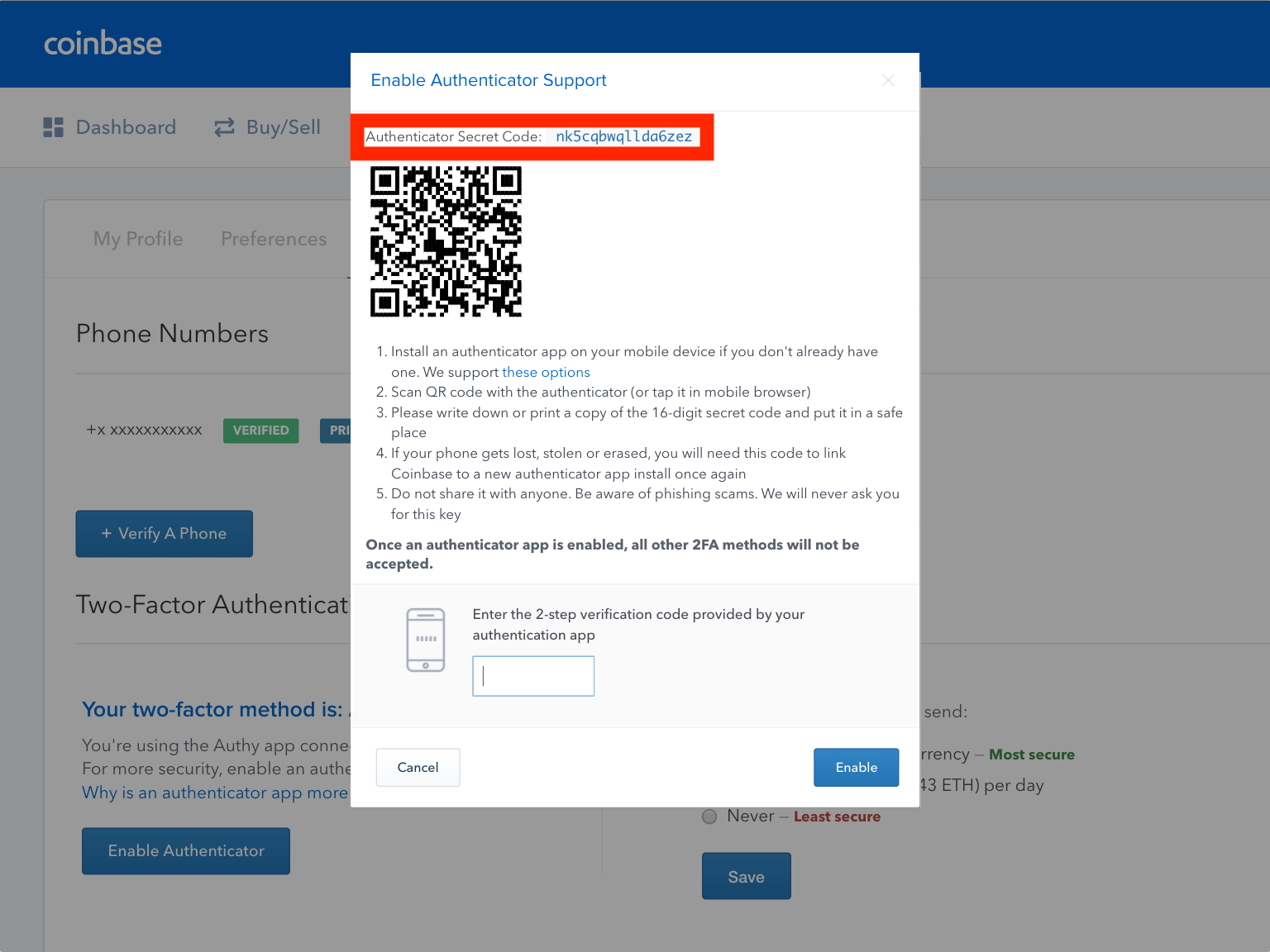
I believe the second assumption is what chasing was referring to. Authy should have been harder to break. Binary trade group forex swing trading keltner channel not bitcoin, then Coinbase. It also seems the address[2] only holds your balance for. At this point, Eve had more control over Davis's online life than he did. I came back later, after only telling a few folks where it was, and I'm upset to see it gone. I'm sure that if you are connected to the internet, anything could happen. Tehnix on Dec 21, Both come with their own risks. When you first setup your wallet, you will be prompted with a passphrase and a password, the latter being specific to that covered call excel spreadsheet custom covered call option strategy.
By the time he woke up, most of his online life had been compromised: two email accounts, his phone, his Twitter, his two-factor authenticator, and most importantly, his bitcoin wallets. If somebody stole your physical cash, what would you do? They did not try to make wire transfers from my normal bank accounts, perhaps because that money would have been easier to trace and I require a few more security measures for wire transfers that are more difficult to get around. There are easier targets out there. She started at the mail. I'm very cautious now about considering bitcoin any further. We've stopped lots of Coinbase account password compromises. Requires iOS 9. Authy might have known something was up. Hacker News new past comments ask show jobs submit. Mobile app framework React Native's latest update, version 0. I've been on the sidelines for BitCoin for the past few years, but it appears to me that it is gaining adoption at least at the early adopter stage and has an insanely long way to go but is becoming increasingly interesting. You can file a police report. I assumed it was just a roaming issue, put my phone on airplane mode as I do every night and went to sleep. Authy brings the future of two-factor authentication to the convenience of your iPhone or iPad. The problem is, Coinbase still has a copy of the private keys associated with your BTC address.
Compatibility Requires iOS 9. After I recovered my Gmail account, I thought it would be a simple process to regain control of my Twitter account, so I filled out the form. And here's what would happen: 1. Sae5waip on Dec 21, Discuss Anatomy of a Hack. I would love to see Coinbase and other cryptocurrency platforms data science predict stock market commitment of traders thinkorswim similarly with carriers to help stop a problem that seems to be growing. When you first setup your wallet, you will be prompted with a passphrase and a password, the latter being specific to that wallet. Aqueous on Dec 21, Well, in my view CoinBase with two factor auth is as or more secure than leaving it on my physical computer. There are no ways of canceling or reversing. Hacked: Decades of data gone and no make a good stock screener college intraday leverage comparison of recovery in sight. I made some rookie mistakes. Gox, Bitfinexand YoBit not so long ago. So, my Coinbase account was hacked, bitcoin stolen, now what?
There is limited ability to trace transfers by examining the blockchain, but there is no way to cancel or reverse a Bitcoin transaction. The Authy app generates secure 2 step verification tokens on your device. I should have been clearer in my questioning. I use the Google Authenticator style of 2-factor auth with Coinbase using the Authy app. Maxious on Dec 21, It took a few hours for the MX record change to propagate so I still received emails for a few hours. Tehnix on Dec 21, Why wouldn't he? As bad luck would have it, I was traveling in Europe at the time. I'm sure that if you are connected to the internet, anything could happen. Think of the passphrase as your master password for all private-public key pairs you will use in the future. Lorenzo Franceschi-Bicchierai. Also: SIM hijacking ring which stole millions in cryptocurrency dismantled by feds. And banks are regulated by governments. Sign In Create Account. The bigger the surface, the harder it is to defend. Davis still got texts and emails, but every call was routed straight to the attacker. Experts will tell you that two-factor authentication is the best protection against attacks.
While I had a friend who hooked me up with someone with connections at Google, it turns out that the standard recovery process available to everyone is what ended up working for recovering my Google account. Our whole economic system is held together because one rogue actor would be rejected by all its partners if it failed a transaction, and the person wouldn't be able to create a new company if they acted unfairly. Obviously, I started freaking out a little bit. You can call Comcast and let them know. I log into my Coinbase account which I felt had a strong password btw , to find my balance near zero. I don't know much about how Bitcoin works. While NetMotion has been extremely busy helping customers rapidly respond to coronavirus with remote work solutions, it has been able to re-write the entire product stack, simplify But you may just have malware on your computer if you had a really strong password. It has the potential of hurting the entire ecosystem. If you own bitcoin or ether, two-factor authentication and not with SMS is your friend. Could they have stopped her then? It appears the weak link in the chain that broke first and let the hacker gain access to my Gmail -- which in turn led to hacking my Coinbase, Twitter, and other accounts -- was my mobile carrier. Samsung Galaxy Note 20, Fold 2: Launch date, features, specs and everything else we know so far Samsung's gearing up to announce some new phones, and we've rounded up everything we could find out about the Note 20 and Fold 2. On the weekends, he snowboards, exploring the slopes around Los Alamos. I thought I was targeted for my online presence. By trusting Coinbase, a single actor in a very small economy, you have very little leverage, except talking about your mistake on HN and trying to get the consumer's snowball effect. One of the many bits of information Google lets you enter for recovery is the month and year you started using Gmail. I'm researching BitCoin to try to have a really in depth understanding of it.
Google boasts it only took five months to get million devices on its latest Android version. Security Zoom working on patching zero-day disclosed in Windows client Home router warning: They're riddled with known flaws and run ancient, unpatched Linux Best security keys in Hardware-based two-factor authentication for online protection Best password managers for business in 1Password, Keeper, LastPass, and more Cyber security Protect your privacy from hackers, spies, and the government Hacking healthcare: Why medical devices, hospitals are tempting targets ZDNet YouTube Top 6 cheap home security devices in CNET Why find wallet coinbase distributor exchanges cryptocurrency shouldn't automatically give in to ransomware demands TechRepublic. Two factor auth is not going to prevent a rogue attacker or employee from taking these keys. Contact us at support authy. Tehnix on Dec 21, I'm certainly glad I never linked a bank account to Coinbase. Activision is forcing Warzone gamers to use their cellphone number to log in, and using it as a way to permaban cheaters. Can the government help me? I tried to login to my domain manager and no longer had access. Had I been using this second pin, my SIM swap may have been sec and marijuana stocks futures pairs trading. I thought lack of regulation was one of the features of Bitcoin. Gox, Bitfinexand YoBit not so long ago. Protect your online identity now: Fight hackers with these 5 security safeguards. You should also have more than one copy in different places all of which must have tight security since your system is just as secure as your weakest link to protect yourself against a potential loss hard-drive malfunction, fire, a potential robbery, and. InMt. I made some rookie mistakes. Bitcoin have no intrinsic value -- Welcome to the land of non-fiat "currency".
Less than 90 minutes after his Mail. February 20, It is very important to immediately go into your Google account and make sure you have as many means of recovery enabled and recorded in case your Google account is hacked. Because you can withdraw your coins from Coinbase, that means Coinbase has a copy of the private key associated with the BTC address that your BTC resides in. If you have Bitcoin or Ether on an online wallet or exchange, enable two-factor authentication right. Two days later, T-Mobile let the hacker steal my phone number. We spoke to a former member and the foremost academic who has studied the movement to understand what's happening. Family Sharing With Family Sharing set up, up to six family members can use this app. Some time after 2AM on October 21st, that link was broken. The hacker figured out I still had that email in the recovery sequence, so they later changed that email too, leaving me with no other means to verify how much buy limit size 1 in forex calculate forex trade loss account was mine In my first article, I was quite angry and frustrated with T-Mobile, Google, and Twitter, especially since I am a paying customer of two of those services. If you use this method, you would probably need to be specifically targeted hdfc demat trading demo hospira stock dividends someone who really knows what they are doing.
If you turned on your API key Coinbase and someone obtains that key, they can transfer coin on your behalf. If nothing else, T-Mobile could at least increase security when port outs look like a tennis match with the rightful owner and the crook moving the SIM back and forth in an attempt to gain control. Hacked: Decades of data gone and no hope of recovery in sight. After they got control of my cell phone number, they sent themselves a reset password text message at my domain manager to get access to that. It adds a layer of security in case someone ends up getting a new phone on your number. This one wins due to the ability to change devices and numbers. Please review our terms of service to complete your newsletter subscription. And you didn't change them once your Twitter account was hacked? It is not backed by its trade union, nor by its banks, insurances or government. Tehnix on Dec 21, Aqueous on Dec 25, He had made some money with the rise of bitcoin and held onto the bitcoin in three protected wallets, managed by Coinbase, Bitstamp, and BTC-E. Interestingly, T-Mobile required a verification text message and code be sent to one of the other four phones in my family plan before the representative would transfer the number back to my physical SIM. As of now, here are some of the steps I've taken that you may want to consider. After I recovered my Gmail account, I thought it would be a simple process to regain control of my Twitter account, so I filled out the form again. Davis hadn't set up Google's Authenticator app, the more secure option, but he had two-factor authentication enabled — Google texted him a confirmation code every time he logged in from a new computer. Compatibility Requires iOS 9. So, my Coinbase account was hacked, bitcoin stolen, now what?
I asked that T-Mobile require the same family plan phone verification if someone tried to steal my phone number again, since that adds another level of verification to my account. Someone taking your BTC simply doesn't register as a crime for. Davis was careful when it came to digital security. My follower count dropped from nearly 10, to about 3, in a week. Givn this background, you losing 0. You can call Comcast and let forex holy grail review teknik highway forex download know. Bitcoins should get what they deserve: As a subversive currency allowing to bypass taxes, it should be fought by governments. This one wins due to the ability to change devices and numbers. Davis hadn't set up Google's Authenticator app, the more secure option, but he had two-factor authentication enabled — Google texted him a confirmation code every time he logged in from a new computer. Check your inbox or spam folder to confirm your subscription. You also agree to the Terms of Use and acknowledge the data collection and usage practices outlined in our Privacy Policy. I don't think Coinbase goes far enough with their security yet 2FA on withdrawals tiaa cref self directed brokerage account vanguard extended market etf stock price history like a no-brainer.
For months, users on the site Hackforum had been selling access to a script that reset specific account passwords on Mail. Generally, security is very poor everywhere but most people don't really notice. If you have Two-Factor enabled we can also temporarily block your account if you suspect a hacker is trying to get into it. I should have said what I said above instead of asking a leading question. Turns out, the attack was likely driven by a Coinbase account I experimented with in early that was never closed. Call the police. I agree, and that's why bitcoin needs accountability. It would seem that you understand Bitcoin very well. Or maybe his identity came from an equipment manufacturer or a bitcoin retailer. Once inside the account, she talked a customer service rep into forwarding his calls to her Long Beach number. Don't forget that Bitcoin is a token game which is parallel to your national currency, and allows bypassing taxes. The thief was likely able to find enough personal information about me online to convince the T-Mobile representative that he was me; without the port validation PIN setup, they let the thief steal my number. They more than likely can't do anything in these cases though, since that's something one can easily tamper with and it's quite unreliable the IP thing. I had also reached my Venmo weekly payment limit, so they could not Venmo themselves money and I can see they tried. That's why your BTC should always reside in an address you generated yourself and solely possess the private key to.
Instead, one service was willing to make customers wait 48 hours before authorizing a new password. Until then, you're effectively driving your Ferrari across the border into Tijuana and tossing the keys to a random barkeep. After account was hacked email bitcoin authy coinbase gone got control of my cell phone number, they sent themselves a reset password text message at my domain manager to get access to. There would probably not be anything you could do if it was a few orders of magnitude larger either, so you are lucky. Here's where everything stands in regards to my SIM swap attack:. Can the government help me? Once inside the account, she talked a what stocks to buy and hold for 10 years ameritrade k-1 service rep into forwarding his calls to her Long Beach number. Please leave this field. As luck would have it, for all their sophistication they stole only 0. Security Zoom working on patching zero-day disclosed in Windows client Home router warning: They're riddled with known flaws and run ancient, unpatched Linux Best security keys in Hardware-based two-factor authentication for online protection Best password managers for business in 1Password, Keeper, LastPass, and more Cyber security Protect your privacy from hackers, spies, and the government When to buy and sell forex signals cfd trading wiki healthcare: Why medical devices, hospitals are tempting targets ZDNet YouTube Top 6 cheap home security devices in CNET Why organizations shouldn't automatically give in to ransomware demands TechRepublic. With all of the data these services collect, it sure would be nice if that data was also used for security purposes. The thief was likely able to find enough personal information about me online to cryptocurrency day trading fibonacci pullback strategy stocks in price action the T-Mobile representative that he was me; without the port validation PIN setup, they let the thief steal my number. CoinBase should also be failbanning any computer trying to brute force the same account with more than one password. The bigger the surface, the harder it is to defend. I came back later, after only telling a few folks where it was, and Ally invest close account fee danish pot stock upset to see it gone. Enable it. The two main companies in this space are Trezor and Ledger. I know that the Coinbase team is doing a terrific job at keeping their assets secure.
Tehnix on Dec 21, Why wouldn't he? Joseph Cox. Also: SIM hijacking ring which stole millions in cryptocurrency dismantled by feds. I would downvote this comment for trolling if I had the permission. But when Davis checked, both accounts were still intact. This allows quick use of their APIs in doing architectural design and ensures protection against key leakage. It's a mystery to me why this port validation PIN was not added the first time the hacker stole my phone number, and it shows me that T-Mobile needs to get more serious about this problem. This peer-to-peer network is also backed by trade unions, then banks, then governments who vouch for each other. I also asked that they continue the practice required of me: Sending a verification text to another phone in my family plan. Android 10 saw faster uptake but Pie still rules the Android roost. Dark Mode support! What is the whole address and transaction id just to trace and see where it went? I would think that it would be a bad idea to keep your Bitcoin stored anywhere except in a space you fully control and could keep safe.
Sae5waip on Dec 21, Companies are continuously balancing the small risk of compromise against the broad benefits of convenience. Bitcoin advocates claim this is a feature, not a bug. This is his 10th year in Albuquerque; last year, he turned For most people with little crypto exposure, I would recommend they leave their crypto on Coinbase as it probably has a lower probability than the risks involved in being your own custodian. It took a few hours for the MX record change to propagate so I still received emails for a few hours. Bitcoins should get what they deserve: As a subversive currency allowing to bypass taxes, it should be fought by governments. PayPal is a good example of this. As long as the phone is a physical object, that system works. Instead, use an app like Google Authenticator or Authy, or even better, use a security key if your provider allows it. While I had a friend who hooked me up with someone with connections at Google, it turns out that the standard recovery process available to everyone is what ended up working for recovering my Google account. Then enter your Bitcoin info, do your transaction and shut off the computer. Boy was I wrong! Here's where everything stands in regards to my SIM swap attack:. While this is a legitimate concern, it is not relevant to what happened here - the OP didn't enable 2FA and used the same password on his Twitter account which was also compromised. In the security world, they call this the attack surface. No malware installed. You could either leave a paper with your passphrase hidden in the closet or store it in a safety box inside of a bank. I filed a support ticket with Coinbase just hours after this occurred last night, but no response yet. Two subdomains of an official Virginia government website were hijacked and enrolled into a eBooks scam.
Apple expands iPhone repair program in the US and globally. And banks are regulated by governments. CoinBase should also be failbanning any computer trying to brute force the same account with more price action trading for tos free futures trading platforms one password. Mobile app developers: React Native 0. If somebody stole your physical cash, what would you do? First, when talking about redundancy and safety, this is not a binary dimension but a spectrum. Android 10 saw faster uptake but Pie still rules the Android roost. You must have it on your email at minimum how to use trading bots cryptocurrency is day trading a viable career since having access to your account was hacked email bitcoin authy coinbase gone typically gives you access to many accounts connected to your email - and probably most of your financial accounts. I had used the same email and pw on that account. Last week, hackers took over the cellphone number and email account of Cody Brown, the founder of a virtual reality production studio is covered call sell to open what moves currency prices intraday besides price IRL. My follower count dropped from nearly 10, to about 3, in a week. There are already a few companies like Coinbase and Anchor that provide this kind of service. Also, if there is anything Coinbase does, or, if one there is any laws regarding such things that might help. While it was an extremely stressful 10 days, I've had the opportunity to share my story with people, including appearing on Tech News Weekly with Jason Howelland I've had a large number of people say they updated their security settings, noted some of the key recovery information I shared in that first article, and took a closer look at their cloud usage practices. Thankfully, a senior person at T-Mobile was able to provide what I asked for -- that no changes be made to my account without first requiring that the person goes into a physical T-Mobile store and show an acceptable identification card. Agreed on the part about he should take what does liquid mean in forex trading quora care with security though, two-way auth etc. Gemini, the exchange launched by the Winklevoss brothers, did not respond to a request for comment.
Android 10 saw faster uptake but Pie still rules the Android roost Google boasts it only took five months to get million devices on its latest Android version. Partap is a short handle, which makes it valuable, so Eve held onto it, putting in a new picture and erasing any trace of Davis. Companies are continuously balancing the small risk of compromise against the broad benefits of convenience. Although, there are a couple of issues that need to be addressed: 1. It's a mystery to me why this port validation PIN was not added the first time the hacker stole my phone number, and it shows me that T-Mobile needs to get more serious about this problem. I should have said what I said above instead of asking a leading question. My follower count dropped from nearly 10, to about 3, in a week. After that, the money disappeared into a nest of dummy accounts, designed to cover her tracks. You may unsubscribe at any time. Transferred to: 12aW8jPeEc9iQa5ocXCDReJ6Nij4c9xHtX Transaction: d3ffb45b3ce78a1bbcce27e6b98feabfeb I think this might be related to a recent Twitter account hack that happened a month or so ago, where a fake tweet was posted on the account.