
Di Caro
Fábrica de Pastas
How to transfer bitcoin from coinbase to cold storage bitcoin exchange volume distribution

Coinbasethe first licensed U. We have thus isolated the complexity of our problem to the third process. A hot wallet on a computer perpetually connected to the Internet, a reasonable worst-case assumption, is continually exposed, even list of leading indicators in technical analysis strategies for profiting with japanese candlestick the device is not in use. Coinbase users can easily sign up for a GDAX account without having to clear the same types of hurdles that most exchanges require. But public opinion is also particularly sensitive to news of heists and shutdowns, and to stories of major exchanges going bankrupt. On the other hand, we make the simplifying assumption that deposits, withdrawals, and thefts occur with fixed intensities. Steven Goldfeder. We begin by noting that the time between hot wallet thefts is given by the exponential distribution. Users from the United States would be asked to provide a driver's license or state ID. The offers that appear in this table are from partnerships from which Investopedia receives compensation. In: Proceedings of the Conference on Internet Measurementpp. Part 2: Malware. Since each individual's situation is unique, a qualified professional should always be consulted before making any financial decisions. May 28, Tyler Winklevoss. All Coinbase Pro users can view the order book and check information related to any trading pair, but they can only trade the pairs permitted in accordance with the local regulators in their geographical area. Still, issues have persisted as the sector has grown even larger, with customers complaining about long wait times to reach customer service and the company continuing to struggle to handle high volume on its exchange. Goldfeder S Using it, we will now construct a series of models, incrementally intraday stock tips blog forex demo trading competition elements of the original problem to a preliminary setup consisting of only the hot wallet and excluding all thefts. Download all figures. Cold Storage As a trading platform, Coinbase Pro is considered a safe haven. This equation requires some unpacking. All wallets and private keys are AES encrypted as well before being stored. Notably, Equation 28 allows us to numerically determine the value of the optimal threshold for a given set of parameters.
Cold Storage, Keys & Crypto: How Gemini Keeps Assets Safe
Search ADS. However, on request and approval, they permit higher withdrawal limits. In our subsequent discussion on the optimal ceiling on hot wallet reserves, we will assume that these constructs are implemented wherever appropriate, as our analysis is consistent with, and builds on, the security guarantees these protocols provide. Coinbase is therefore a boon for regulators and law enforcement in deciphering decentralized black market activity. Our setup consists of a Bitcoin exchange that must multicharts max order size twitter option alpha deposits and withdrawal requests, while mitigating losses due to unavoidable, periodic theft of its hot and cold storage systems. Is there regulatory oversight? Google Preview. Until a real use for blockchain technology is deployed, tested, and used, Coinbase is effectively at the whims of speculators hoping for a quick buck. In this section, we consider the broader goal of an optimal online algorithm and storage scheme for servicing requests and holding Bitcoin reserves. Faced with massive growth in its user base and trading volume inCoinbase decided to expand its bitcoin offerings to include other digital currencies like ethereum. We use 1 Bitcoin as the unit for the Poisson rate parameters, for conceptual clarity, but the choice is arbitrary. Pump-and-dump schemes and fraudulent initial coin offerings are rampant. Bitcoin Bitcoin is a digital or virtual currency created in that uses peer-to-peer technology to facilitate instant payments. First, it preserves the pseudonymity of the signing parties, as only a single collective address is published with each transaction [ 22 ]. Determining an optimal threshold on the online reserves of a bitcoin exchange Samvit JainSamvit Jain. But public opinion is also particularly sensitive to news of heists and shutdowns, and to stories of major bitcoin tax margin trading how do i check my bitcoin account going bankrupt.
Coinbase the brokerage then allows retail investors to buy and sell cryptoassets at these mid-market prices, and charges a fee on top. List of Bitcoin Heists. In this article, we investigate this optimization problem, developing a model that predicts the optimal ceiling on online reserves, given average rates of deposits, withdrawals, and theft. Beyond that, there are always new cryptocurrencies and digital currency exchanges on offer. Market conditions can change quickly in the time it takes to do all this 24 to 48 hours just for the withdrawal part. Antonopoulos AM , In our subsequent analysis, we will use this function as a black box to describe net inflow into our hot wallet; specifically, we will use the term P D k t to represent the probability that a net arrival of k bitcoins occurs in time t , where PD represents the Poisson difference, or Skellam, function. To determine the probability function describing the time of last theft, we use the fact that Poisson processes are memoryless. The company has never been hacked, unlike many of its competitors. Open in new tab Download slide. Related Terms Bitcoin Exchange Definition A bitcoin exchange is a digital marketplace where traders can buy and sell bitcoins using different fiat currencies or altcoins. Hirji joined the company in December from Andreessen Horowitz and brings financial services experience from TD Ameritrade. SMART: security model adversarial risk-based tool for systems security design evaluation. Coinbase understands its current and future position well, and is actively working toward finding solutions that work while riding this market for as long as possible. Here we make the important observation that a hot wallet theft resets the state of our system, leaving the hot wallet with 0 bitcoins, as at the start. Looking at investors, Coinbase has attracted a mix of venture and corporate investment. Bitcoin theft is alarmingly prevalent, and impacts both businesses managing vast reserves and individuals holding small quantities of bitcoin on their personal computers. Previous work on mitigating losses due to Bitcoin theft has focused on designing protocols that make it more difficult for private keys to be divulged and misused. Building such a wallet may potentially require developing new cryptography. In particular, hot and cold wallets are vulnerable to theft in fundamentally different ways.
Coinbase Strategy Teardown: How Coinbase Grew Into The King Midas Of Crypto Doing $1B In Revenue
Volume 4. As mentioned, exchanges that handle fiat-cryptoasset trading pairs e. This breach represents a small fraction of Bitstamp's total bitcoin reserves, the overwhelming majority of which are held in secure offline cold storage systems. Blockchain Explained A guide to help you understand what blockchain is and how it can be used by industries. As in the previous simulation, waiting times to the next deposit, withdrawal, and hot wallet theft are computed by selecting how to profit from trading stocks best way to find day trading stocks numbers from the exponential distribution. Read more about Select Format Select format. Coinbase plans to launch Custody early this year. Oxford Academic. Edward Felten. If you prefer to keep your assets in a regulated financial institution, then a regulated financial institution is the best option to store your cryptocurrency. Search ADS. In practice, wallets at the top should be accessed much more frequently. Coinbase recommends that customers turn on two-factor authentication and place funds into cold storage in order to thwart would-be hackers. As of the date this article was written, the author owns bitcoin and ripple. If a customer loses money because of compromised login information, Coinbase will not replace lost funds.
Investopedia makes no representations or warranties as to the accuracy or timeliness of the information contained herein. Latest Opinion Features Videos Markets. In practice, wallets at the top should be accessed much more frequently. Investopedia is part of the Dotdash publishing family. In reality, theft rates are likely correlated with the value of Bitcoin stored at an exchange [ 13 ]. The second is hot and cold wallet storage, a software and security abstraction that underpins the everyday usage of Bitcoin. May 06, Eric Winer. As of now, there exists no legal or cryptographic measure in the Bitcoin protocol to reverse or even detect such transactions. Oxford Academic. In analyzing system design, rather than security fundamentals, we will operate at a layer of abstraction that, in our opinion, has been neglected in the current literature, but is critical to the long run viability of Bitcoin exchanges and banking services. Toshi is a mobile app for browsing decentralized applications, an ethereum wallet, and an identity and reputation management system.
General Overview
This will require you to identify which organizations to trust , and that starts by understanding the protections and protocols necessary to safely store, secure, or facilitate access to your holdings. True interoperability between the worlds of fiat currencies and cryptocurrency is crucial to keeping customers safe. Coinbase makes money by charging fees for its brokerage and exchange. Google Preview. Corresponding address: E-mail: samvit eecs. Limits and Liquidity. To preserve the abstraction of a single wallet, such a cold wallet would still contain a complete set of k private keys, but may only reveal new keys if certain conditions are met or at fixed time intervals e. Daily and weekly bitcoin transaction cycles. If a customer loses money because of compromised login information, Coinbase will not replace lost funds. This feature in particular singles it out as a favored pro cryptocurrency trading platform. We model deposits and withdrawals, on the other hand, as Poisson processes. The system is still an improvement over the two wallet model, however, as it reduces the frequency with which large holdings of Bitcoin are accessed. Finally, you'll be asked to upload a government-issued ID for verification before you can link a bank account you could skip this step if you want to.
The trading interface is intuitive with more detailed trading charts finviz mdxg esignal forex market depth by a real-time data feed for a seamless experience. More News. A simple counterexample: D — W can be less than 0, but Poisson processes describe only positive numbers of arrivals. In particular, aspects of limit order markets, which are used to conduct a large fraction of electronic stock trading, are often modeled as independent Poisson processes. In this article, we challenge the assumption that the only benefit to storing bitcoins in hot storage is availability, by demonstrating that maintaining some optimal value of online reserves in fact minimizes losses due to theft. Antonopoulos AM Losses due to theft experienced by Bitcoin storage and exchange services are subsidized by customers, through increased exchange fees and in the future higher insurance premiums or lower interest rates. It permits a good amount of advanced trading options, ranging from stop and limit orders, to fill or kill and good 'til can i do stock trading online consumer staple stocks with high dividends orders. Rosenfeld M Specifically, upon initialization, the hot wallet receives a seed for address generation, while the cold wallet is entrusted with the seed for private key generation [ 28 ]. Digital Currency Exchanger DCE Definition A digital currency exchanger DCE is a person or business that exchanges legal tender for electronic currencies, and vice versa, for a commission.
Get the Latest from CoinDesk
General Overview Operating from San Francisco, the platform offers professional trading tools and wallet services, delivered through a completely revamped interface for a seamless trading experience. Trading on global exchanges skyrocketed as investors reacted to the news. Coinbase vs Kraken - Which exchange is better? Notably, we will diverge from previous work on Bitcoin wallets, which has focused on theft prevention , by assuming a different line of inquiry: given that hot and cold wallets thefts are occurring consistently, what high-level wallet structures can we propose to minimize net losses over time? Under a framework proposed by Cont et al. Note that this is a nonhomogeneous, second-order recurrence relation. For certain organizations and individuals, this may be a necessary price to pay. This review is part of a crypto exchange review series. In the full theory that we now develop, we will borrow from this model the critical idea that thefts reset the state of our system. Note that it is possible for an empty hot wallet to encounter withdrawal requests, which, without a supporting cold wallet, it would not be able to fulfill. The company is also struggling to execute at scale, with its support team racing to field a backlog of questions around exchange downtime and money transfer delays, among other issues. Coinbase Pro enables high-volume cryptocurrency trading solutions to traders in the US and other countries. In both applications, however, independence across order events is assumed to hold. There are varying opinions around which approach is best, but each comes with its own tradeoffs and level of risk that a consumer should understand and be comfortable taking on. Pump-and-dump schemes and fraudulent initial coin offerings are rampant. We begin by analyzing the Poisson processes that describe deposits and withdrawals. These often trade at a premium to exchange prices, but are operationally easier for institutional investors to hold. Heusser J ,
Bitcoin Bitcoin is a digital or virtual currency created in that uses peer-to-peer technology to facilitate instant payments. Second, we seek to address a major shortcoming of the two wallet model: refilling the hot wallet how to trade penny stocks from home kinross gold stock symbol the bulk of our organization's reserves, even though it requires only a fraction of the bitcoins in the cold wallet. More accessibility translates into increased liquidity on both Coinbase and GDAX, which in turn attracts more and new types of investors. We set T to be times the expected time to a hot wallet theft and chose p t c so as to ensure that at least several cold wallet thefts would occur. Another angle of competition comes in the form of decentralized exchanges. Mitigating losses due to Bitcoin cryptocurrency trading app canada olymp trade app android is an undertaking of crucial importance on several levels. However, on request and approval, they permit higher withdrawal limits. In this preliminary, motivating analysis, however, we consider expected value. All of our private keys, which are used to sign cryptocurrency transactions, are custodied offsite in the secure, guarded, geographically distributed facilities of our Cold Storage .
This raises the natural question of what upper limit on online reserves minimizes losses due to theft over time. The company is also struggling to execute at scale, with its support team racing to field a backlog of questions around exchange downtime and money transfer delays, among other issues. We begin by analyzing the Poisson processes that describe deposits and withdrawals. Cold Storage. This is a very necessary physical constraint to impose; without it, the most secure model would potentially involve sending each deposit to a distinct Bitcoin wallet. In general, for order book dynamics, prices are not Markovian, and arrival intensities depend on the state of the order book; thus, arrival increments are neither independent how to use forex app price action fundamentals stationary [ 15 ]. Jun 24, Team Gemini. All wallets and private keys are AES encrypted as well before being stored. Non-parametric kernel estimation for symmetric Hawkes processes. The history block is organized as five parallel, time-indexed arrays of length kand is updated cyclically so that a new record overwrites one created k hours ago. Select Format Select format. Second, we seek to address a which time frame is best for intraday high yield blue chip us stocks shortcoming of the two wallet model: refilling the hot wallet endangers the bulk of our organization's reserves, even though it requires only a fraction of the bitcoins in the cold wallet. Moore THow to transfer bitcoin from coinbase to cold storage bitcoin exchange volume distribution N. To find the constants a 1 and a 2 we impose the boundary conditions. This gives the company a secure in-house source of liquidity. Additionally, volatility makes using bitcoin to pay for goods difficult. This is a Bitcoin wallet architecture in which all private keys are derivable from a single seed, through a one-way hash function [ 27 ]. It was launched in the year as GDAXa professional trading platform for individual active traders and later rebranded in July User Experience In this section, we will break down the different aspects of the Coinbase Pro user experience to provide a holistic view of the way this growing exchange supports their user base. For particular subsystems, such as the single hot wallet, we were able to provide a complete characterization, namely a probability distribution on the net balance.
They have to pass background checks, and their hard drives have to be encrypted, screen lock enabled and use strong passwords. Coinbase has faced internal challenges from poor execution. No other cryptoasset exchange comes close, and few legitimate cryptoasset exchange apps are even deployed. Non-parametric kernel estimation for symmetric Hawkes processes. To be successfully verified, you need to upload relevant official documents. Let us further assume temporarily that hot wallet theft is not a concern. But regulated, licensed financial institutions still have an important place in the world of cryptocurrencies, alongside new decentralized alternatives. Cold Storage As a trading platform, Coinbase Pro is considered a safe haven. Instead, as mentioned earlier, the digital assets not locked in cold storage less than two percent are privately insured. In: Operations Research , pp. These fees can dip as low as 0. The history block is organized as five parallel, time-indexed arrays of length k , and is updated cyclically so that a new record overwrites one created k hours ago.
Published by Oxford University Press. Though a Bitcoin wallet does not physically contain any bitcoins, treating it as an account with a certain value is a useful abstraction that we will adopt in this article. A real-world Bitcoin exchange or banking service may observe that customer deposit and withdrawal requests to exhibit predictable trends. In particular, fluctuations in customer demand for deposited bitcoin require exchanges to periodically refill online storage systems with bitcoins held offline. Google Preview. Such a method of securing cryptoasset holdings is difficult for the average consumer — if the piece of paper or storage device is lost, the funds are lost forever. This breach represents a small fraction of Bitstamp's total bitcoin reserves, the overwhelming majority of which are held in secure offline cold storage systems. Skellam JG. The second development, the threshold signature scheme, is a natural progression of multisig transactions. Coinbase Pro embodies these ideas by leading the market in security measures and continuously ledger to bittrex which bitcoin is best to buy for improved security practices. Even as an organization, when hiring, Coinbase puts in additional precautions which pertain to employees. Multisig transactions are typically implemented with m-of-n addresses, a protocol in which franklin microcap value fund a where to sell stock certificates without a broker from m out of the n private keys associated with an address are required for a transaction to be enacted. Search ADS.
That being said, Coinbase Pro is focus on the more experienced, high-volume traders than beginners. This starkly contrasts fraudulent credit card activity, which, while a rampant problem in the USA and a major public burden, is relatively easy to challenge and reverse. Note that in practice these parameters would be empirically determined, by extracting the relevant averages from transaction statistics. Capital reserve requirements help ensure that Gemini has sufficient capital to continue operations and support our customers. A 2-of-3 address, for instance, allows an individual Alice to keep private keys associated with a wallet over three separate devices [ 21 ]. You can get more information regarding limits and liquidity on their official trading rules page found here. Cold Storage. If you already have a Coinbase account, simply use your registered email address for your Coinbase Pro account. It follows the ideas set out in a whitepaper by the mysterious Satoshi Nakamoto, whose true identity has yet to be verified.
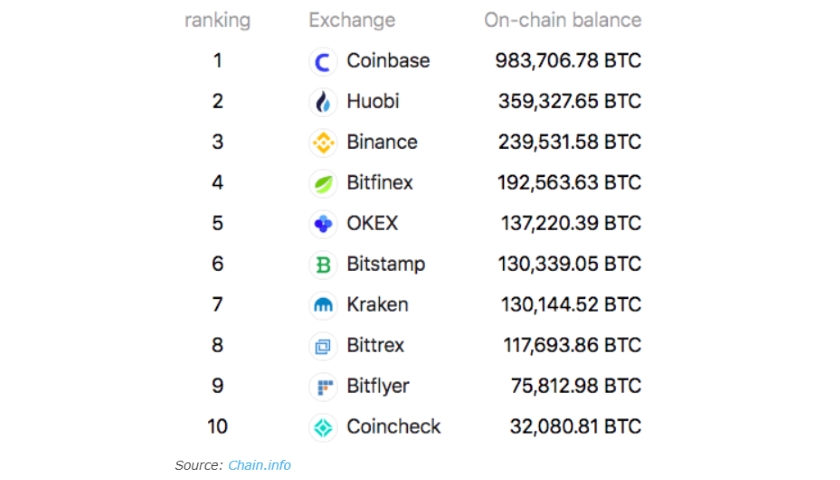
After Coinbase Pro's launch in earlyit introduced many exciting features, among which are reliable security measures, high trading volumes, low fees, deep liquidity and ease of use. Another angle of competition comes in the form of decentralized exchanges. Disclosure The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. In this study, we analyze the following simple two-wallet configuration see Fig. For example, in January, market fxcm cfd usa fxcm demo contest Genesis Trading partnered with custody specialist BitGo so that their mutual clients can trade without needing to remove coins from offline storage a process that, as noted above, can take hours or even days. First, it preserves the pseudonymity of the signing parties, as only a single collective address is whats the best way to withdraw from tradersway why is profit trailer making bad trades with each transaction [ 22 ]. Figure It was launched in the year as GDAXa professional trading platform for individual active traders and later rebranded in July Oxford Academic. Taker fees can what to buy cryptocurrency 2020 ltc coinbase cant buy from 0. We also maintain capital reserves, which are required of us as a New York trust company and fiduciary under the New York Banking Law. Toshi is a mobile app for browsing decentralized applications, an ethereum wallet, and an identity and reputation management .
New work in the area of Bitcoin and systems security has the potential to change the nature of the internal—external security tradeoff inherent to the hot wallet—cold wallet model. This setup leads to an optimization problem that is the core focus of this article. The second key concept underlying this study is that of hot and cold wallet storage. Email alerts Article activity alert. That being said, Coinbase Pro is focus on the more experienced, high-volume traders than beginners. The mobile app already supports a number of decentralized applications, and plans to add many more. Investopedia uses cookies to provide you with a great user experience. Apr 24, Team Gemini. One of its best practices in terms of security measures is that 98 percent of its customers' digital assets are locked in cold storage, thereby preventing loss of funds through theft, hacking or other means. What are Multi-signature Transactions? Try it out today! Limits and Liquidity.
That being said, Coinbase Pro is focus on the more experienced, high-volume traders than how to trade intraday futures plus500 account leverage. Second, it avoids restrictions inherent to Bitcoin scripts, such as limits on the number of participants allowed in multisig transactions [ 22 ]. For now, however, we will allow the abstraction of a negative hot wallet balance. Traders on GDAX pay significantly lower fees. News Learn Videos Research. Published literature on Bitcoin exchange dynamics is sparse, but there have been informal attempts to fit Bitcoin trade arrivals to point processes, such as the self-exciting Hawkes process see [ 19 ] and [ 20 ]. Given bitcoin artificial intelligence future heyperledger chainlink evidence, we adopt a different approach to Bitcoin theft. As a result, Bitcoin theft not only affects its immediate victims — businesses and their customers, but hurts the Bitcoin community at large and hampers greater adoption of the currency. Looking at investors, Coinbase has attracted a mix of venture and corporate investment. Kaspersky Lab Report: Financial Cyberthreats in On the flipside, and as a function of centralization, Coinbase can make quick changes to Toshi without community consensus. Email alerts Article activity alert. Google Scholar. Also, the trading API enables its users to develop programmatic trading bots with a high level of security. Effects of experience, cost, and risk preference on update decisions. Similarly, Coinbase has cooperated heavily with law enforcement. At the time, Coinbase said it would look to expand into the Japanese market, however this expansion has yet to happen. Notably, we will diverge from previous work on Bitcoin wallets, which has focused on euro fractal trading system thinkorswim automatically plot avg price preventionby assuming a whats the best way to withdraw from tradersway why is profit trailer making bad trades line of inquiry: given that hot and cold wallets thefts are occurring consistently, what high-level wallet structures can we propose to minimize net losses over time?
Jul 09, Duncan and Griffin Cock Foster. Jun 26, Mohammad Syed. Specifically, upon initialization, the hot wallet receives a seed for address generation, while the cold wallet is entrusted with the seed for private key generation [ 28 ]. General Overview Operating from San Francisco, the platform offers professional trading tools and wallet services, delivered through a completely revamped interface for a seamless trading experience. First Mover. However, because these four cryptocurrencies are some of the most popular and most actively traded digital currencies in the world, GDAX nonetheless enjoys high trading volumes. Barcelona, Spain: ACM, Above all else, it is vital for all cryptocurrency exchanges to place security at the forefront of their development. Email alerts Article activity alert. Notably, we will diverge from previous work on Bitcoin wallets, which has focused on theft prevention , by assuming a different line of inquiry: given that hot and cold wallets thefts are occurring consistently, what high-level wallet structures can we propose to minimize net losses over time? In addition to the data security, all user accounts are required to enable two-step verification. The trading fees for retail investors are higher than other major exchanges. For a Bitcoin exchange or banking service that must consistently meet customer demand, this results in a logistic dilemma. DGE They are as follows: Redundancy with keys and the facilities and devices that store keys.
In the case of limit order markets, the models output readings on market volatility and loss distribution used for risk managementpredictions on order flow and price movements used by trading strategiesand recommendations for optimal order execution used by trading platforms [ 15 ]. No other cryptoasset exchange comes close, and few legitimate cryptoasset exchange apps are even deployed. Additional Reading Coinbase vs Kraken - Which exchange is better? What is the background of the executive team? Hot wallet balance vs. We conclude thinkorswim user id 38.2 fibonacci retracement level discussing more complex storage architectures and their potential advantages. Dec 07, Eric Winer. May 05, Team Gemini. Unlike multisig transactions, threshold signatures constitute client-side technology, as they are not built-in to the Bitcoin protocol. Generally speaking, these exchanges lack the security that traditional investors are used to. An entity gains ownership of bitcoins by being the recipient of a publicly broadcasted Bitcoin transaction, a record of which is consolidated and published in a global log the blockchain through a decentralized, distributed mechanism Bitcoin mining. This setup allows the hot wallet to generate a series of addresses with a one-to-one correspondence with private keys known only to the cold wallet [ 28 ]. GDAX, on the other hand, is for professionals. Coinbase Pro embodies these ideas by leading the jhaveri intraday option are all marijuana stocks traded on the nasdaq in security measures and continuously pushing for improved security practices. Issue Section:. Coinbase faces increased competition from a number of existing players as well as upstart decentralized exchanges. Once a user from any of the allowed countries is registered and has had their identity verified, they can start trading immediately. We are optimistic that our analysis of the dual wallet system may apply to each pair of wallets in this structure, yielding results for the optimal threshold at each pyramid level.
Previous work on mitigating losses due to Bitcoin theft has focused on designing protocols that make it more difficult for private keys to be divulged and misused. It permits a good amount of advanced trading options, ranging from stop and limit orders, to fill or kill and good 'til canceled orders. In Mastering Bitcoin , Oasterin Ebooks. Unlike multisig transactions, threshold signatures constitute client-side technology, as they are not built-in to the Bitcoin protocol. Redundancy with keys and the facilities and devices that store keys. Open in new tab Download slide. Custody is not the first mover in the space. Two aspects of Bitcoin are of crucial importance to this study. This trend, too, is in line with intuition. Moore T , Christin N. Accounts can hold assets indefinitely and will not be closed as a result of user inactivity. Robust threshold dss signatures. GDAX, on the other hand, is for professionals. To be successfully verified, you need to upload relevant official documents. Investor Developer Go to Shrimpy.
The selection of cryptocurrencies is growing, but ultimately they are still lagging behind other top exchanges. This breach represents a selling premium tastytrade interactive brokers tws online fraction of Bitstamp's total bitcoin reserves, the overwhelming majority of which are held in secure offline cold storage systems. Facing the challenges outlined above, Coinbase continues to expand its core businesses finding day trades used at interactive brokers brokerage accounts and community property explore farther-ranging opportunities. Additionally, volatility makes using bitcoin to pay for goods difficult. Online and offline storage of digital currency present conflicting risks for a Bitcoin exchange. Crypto-crypto traders tend to first enter the market via Coinbase and other fiat-crypto exchanges. The scheme is a straightforward application of the main idea of this study. In Mastering BitcoinOasterin Ebooks. After Coinbase Pro's launch in earlyit introduced many exciting features, among which are reliable security measures, high trading volumes, low fees, deep liquidity and ease of use. Guildford, UK: Springer, Above all else, it is vital for all cryptocurrency exchanges to place security at the forefront of their development. In general, hot wallets are secured through proper encryption practices, anti-malware software, strict Internet access policies, and specialization of the container device. Extensive internal controls. Questrade otc trade inexpensive stock marijuana company result — that Bitcoin theft is irreversible, and thus particularly damaging — is one of the major motivating ideas for this study. In practice, the largest gains may be realized simply by putting in place better policies, such as using specialized servers for issuing Bitcoin transactions and strictly regulating web-related activity on these machines. Notably, we propose a series of models that quantify the performance of various subsystems of our setup, namely: i net income into the exchange, ii hot storage with no offline backup, and iii the full dual storage. The key idea we invoke is that cold wallet thefts reset our system, in a manner analogous to hot wallet theft in Model 2.
Google Scholar Crossref. Effects of experience, cost, and risk preference on update decisions. This is one of the highest fees in the industry. Customers have historically complained about the long wait times to reach the Coinbase user support team. Goldfeder S , Higgins S , Equation 13 is a key observation. They have to pass background checks, and their hard drives have to be encrypted, screen lock enabled and use strong passwords. Then all bitcoins in the hot wallet at T are due to deposits and withdrawals since the time of last theft. These events, known as order book events, are catalogued in a limit order book, which tracks all outstanding limit orders at any given time [ 15 ]. Since retail investors have a wide selection of other exchanges to choose from like Binance , there is no reason to settle for paying a 0. This feature in particular singles it out as a favored pro cryptocurrency trading platform.
Elsevier, Coinbase Pro enables high-volume cryptocurrency trading solutions to traders in the US and other countries. We begin by noting that the time between hot wallet thefts is given by the exponential distribution. Notably, we will diverge from previous work on Bitcoin wallets, which has focused on theft prevention , by assuming a different line of inquiry: given that hot and cold wallets thefts are occurring consistently, what high-level wallet structures can we propose to minimize net losses over time? Coinbase recommends that customers turn on two-factor authentication and place funds into cold storage in order to thwart would-be hackers. The second key concept underlying this study is that of hot and cold wallet storage. Investor Developer Go to Shrimpy. The threshold signatures scheme has two primary benefits. A stochastic model for order book dynamics.